Get acquinted with GPG
-
4 mins read
Generate GPG key pair
gpg --full-generate-key
see output
╰─➤ gpg --full-generate-key
gpg (GnuPG) 2.4.5; Copyright (C) 2024 g10 Code GmbH
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(9) ECC (sign and encrypt) *default*
(10) ECC (sign only)
(14) Existing key from card
Your selection?
Please select which elliptic curve you want:
(1) Curve 25519 *default*
(4) NIST P-384
(6) Brainpool P-256
Your selection?
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 1y
Key expires at Tuesday 08 April 2025 04:58:41 PM UTC
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Mr Anonymous
Email address: anonymous@secmail.com
Comment: hello there !
You selected this USER-ID:
"Mr Anonymous (hello there !) <anonymous@secmail.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: revocation certificate stored as '/home/user/.local/share/gnupg/openpgp-revocs.d/BB1727BCB8CD2B3F7D680BAB60C6E687D3A01803.rev'
public and secret key created and signed.
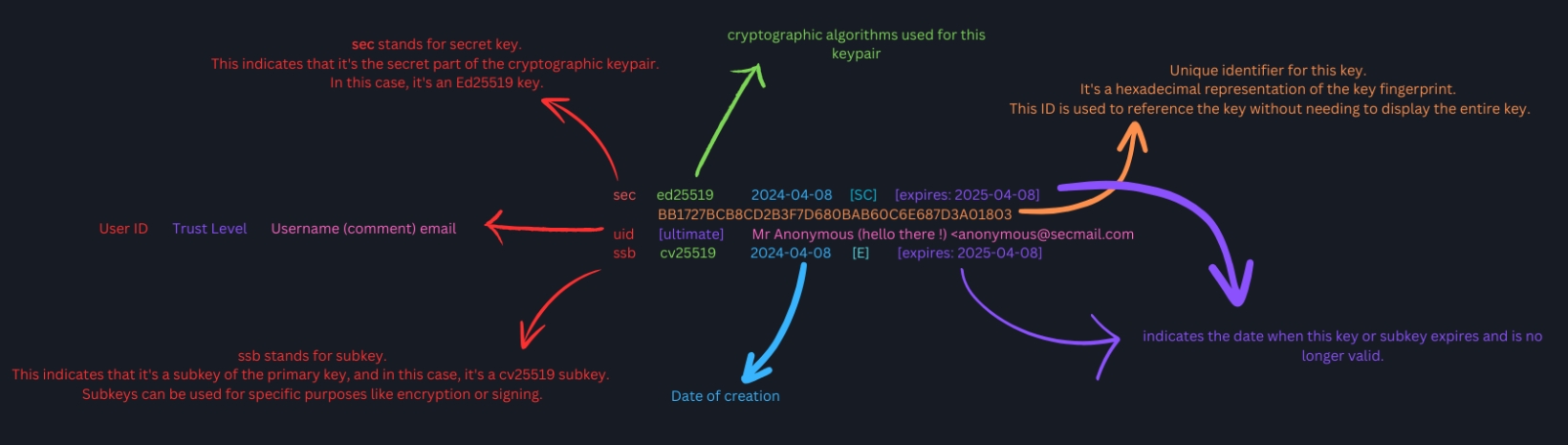
pub ed25519 2024-04-08 [SC] [expires: 2025-04-08]
BB1727BCB8CD2B3F7D680BAB60C6E687D3A01803
uid Mr Anonymous (hello there !) <anonymous@secmail.com>
sub cv25519 2024-04-08 [E] [expires: 2025-04-08]
Explanation of inputs
Key Type
Type of algorithm to use for key generation
-
RSA:
- RSA was default for a long time and is still widely used.
-
EDCCA:
- EDCCA is the new default, which uses elliptic curve cryptography for encryption.
- It produces smaller key sizes, which are faster than RSA with the same level of security.
- [RECOMMENDED]
Expiration Date
- Pick some expiration deadline
- YES, u can put 0 for a key that never expires but it is NOT recommended
- YES, u can extend the deadline of ur key. So no need to panic about doomsday :)
Name, Email, Comment
- Enter your name of the identity u want to create with this gpg key
- NO, name and email do NOT have to be real. No automated emails will ever be used to communitcate
- However other people may use the email from here to communicate back to u if u want
- Comment -> just a comment. No further comments :)
Understanding Key Format
Importing Keys
Copy the GPG key andsave it to keyfile.txt file and run.
gpg --import keyfile.txt
Or a fancier and better way to do the same
xclip -o | gpg --import
To view the imported keys -
gpg -k # list all public keys
gpg -K # list all private keys
Export Keys & Backup
To export/share your public key
gpg --export --armor fingerprint/username
Backing up ur secret/private keys
gpg --export-secret-keys > secretkeys.gpg
Save it in a secure location and restore it with --import command.
Encrypt/Decrypt Messages
Encryption
gpg -e -s -r username/email/fingerprint --encrypt-to my_username --armor ./message.txt
Flag Explanations
- -e : encrypt
- -s : sign the message with my private key, optional but good practice to sign your messages
- -r : recipient - they guy who u are encrypting for
- –encrypt-to : optional, encrypts the message with your key so u can also decrypt the message
- -a : armor, use ascii output instead of binary output.
Decryption
gpg file.txt
xclip -o | gpg
Signing & Verifying Messages
This to produce a binary signed message “file.gpg”
gpg -s file.txt
This to produce a ACII signed message “file.asc”
gpg --clear-sign file.txt
To verify someone’s signed message.
gpg --verify file.txt